sqlmap 使用篇
创始人
2025-05-28 17:02:50
0次
文章目录
- 前言
- 一、sqlmap 使用
- “信息参数”
- 目标参数
- request 参数
- 二、使用示例
- 总结
前言
理解了sqlmap的原理,那么就可以无所畏惧地使用sqlmap了。sqlmap提供了许功能,这些功能都应该为我们所用,也就是必须提供我们使用方法,或者说接口。sqlmap的功能接口体现在一个个参数上——options。额,,几乎所有的命令行的使用接口都是体现在可传入的参数上
一、sqlmap 使用
sqlmap怎么用?我们直接sqlmap -h,显示如下:
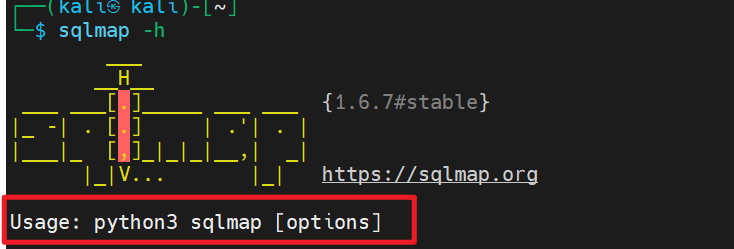
根据提示,sqlmap的用法就是:sqlmap + [options]。sqlmap提供了很多options,也就是可传入的参数。这些options根据不同的用处,组织在一起,就是一个小分组。sqlmap -hh显示所有的可用参数,我们在文末附上。
- Target
- At least one of these options has to be provided to define the target(s)
- 至少提供一个参数来定义目标
- Request
- These options can be used to specify how to connect to the target URL
- 指定如何访问目标URL,即自定义数据包,即自定义HTTP请求报文(文本)
- Optimization
- These options can be used to optimize the performance of sqlmap
- 这些选项用来优化的sqlmap的执行
- Injection
- These options can be used to specify which parameters to test for, provide custom injection payloads and optional tampering scripts
- 这些选项用来指定注入的payload和可选的tamper 脚本
- Detection
- These options can be used to customize the detection phase
- 这些选项用来定制检测阶段
- Techniques
- These options can be used to tweak testing of specific SQL injection techniques
- 微调使用的注入技术
- Fingerprint
- -f, --fingerprint Perform an extensive DBMS version fingerprint 指纹识别
- Enumeration
- These options can be used to enumerate the back-end database management system information, structure and data contained in the tables
- 枚举后端数据库的信息、结构和数据
- Brute force
- These options can be used to run brute force checks
- 暴力破解
- User-defined function injection
- These options can be used to create custom user-defined functions
- File system access
- These options can be used to access the back-end database management
system underlying file system
- These options can be used to access the back-end database management
- Operating system access
- These options can be used to access the back-end database management system underlying operating system
- Windows registry access
- These options can be used to access the back-end database management system Windows registry
- 用于
- General
- These options can be used to set some general working parameters
- 设置一些工作参数
- Miscellaneous:
- These options do not fit into any other category
- 不在其他范畴(分组)的选项
“信息参数”
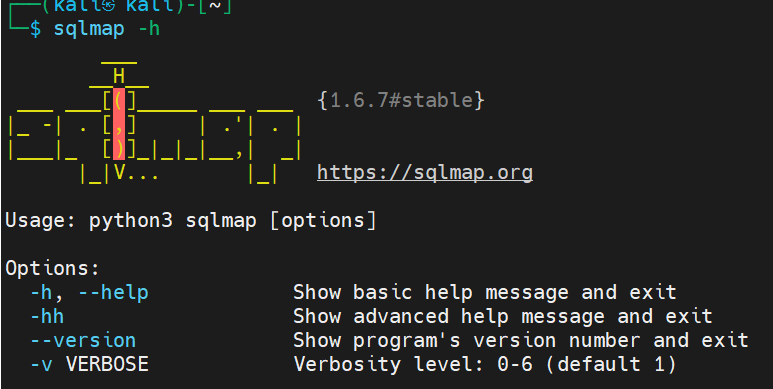
这些选项可以理解为"全局的选项",主要是帮助信息、版本信息和信息的显示级别
-v VERBOSE信息级别:0-6(默认为1),值得具体含义:
- 0:只显示Python错误及严重的信息
- 1:同时显示基本信息和警告信息
- 2:同时显示bug信息
- 3:同时显示注入的
payload - 4:同时显示HTTP请求
- 5:同时显示HTTP响应头
- 6:同时显示HTTP响应页面
目标参数
攻击的目标,至少提供以下的一种类型
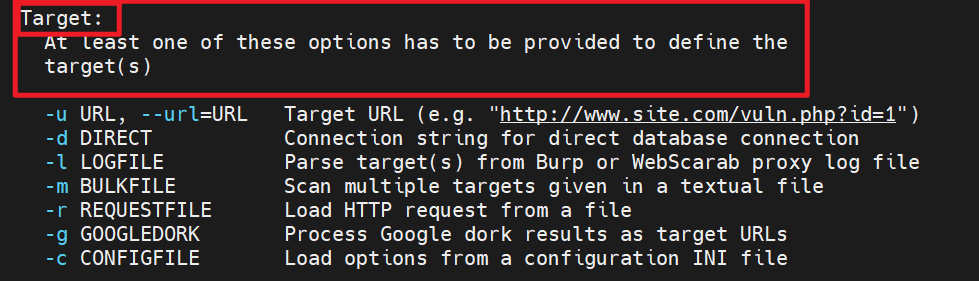
攻击的目标,至少提供一个
-d:直接连接数据库的字符串-u / --url=URL:注入点目标URL-l(LOGFILE):从BurpSuite或Webscarab代理日志中分析目标-x(SITEMAPURL):从远程网站地图(sitemap.xml)文件解析目标-m(BULKFILE):将目标地址保存在文件中,一个行为一个URL地址进行批量检测-r(REQUESTFILE):从文件加载HTTP请求-g(GOOGLEDORK):从谷歌中加载结果目标URL(只获取前100个结果,需要挂代理)-c(CONFIGFILE):从配置ini文件中加载选项
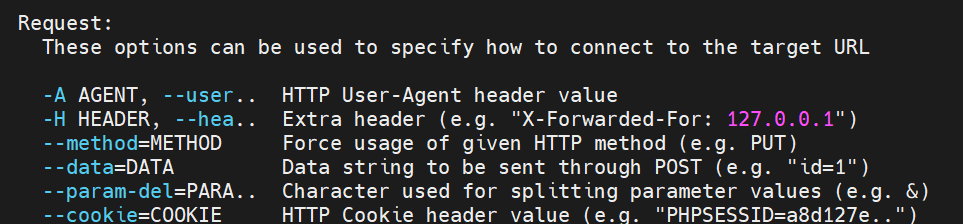
request 参数
这类options用来指定如何连接到目标URL,也就是自定义数据包,也就是自定义HTTP请求报文(文本)
二、使用示例
总结
以下是sqlmap的所有参数选项
┌──(kali㉿kali)-[~]
└─$ sqlmap -h_____H_____ ___[(]_____ ___ ___ {1.6.7#stable}
|_ -| . [,] | .'| . |
|___|_ [)]_|_|_|__,| _||_|V... |_| https://sqlmap.orgUsage: python3 sqlmap [options]
# 选项===========================================================
Options:-h, --help Show basic help message and exit-hh Show advanced help message and exit--version Show program's version number and exit-v VERBOSE Verbosity level: 0-6 (default 1)Target:At least one of these options has to be provided to define thetarget(s)-u URL, --url=URL Target URL (e.g. "http://www.site.com/vuln.php?id=1")-g GOOGLEDORK Process Google dork results as target URLsRequest:These options can be used to specify how to connect to the target URL--data=DATA Data string to be sent through POST (e.g. "id=1")--cookie=COOKIE HTTP Cookie header value (e.g. "PHPSESSID=a8d127e..")--random-agent Use randomly selected HTTP User-Agent header value--proxy=PROXY Use a proxy to connect to the target URL--tor Use Tor anonymity network--check-tor Check to see if Tor is used properlyInjection:┌──(kali㉿kali)-[~]
└─$ sqlmap -hh_____H_____ ___[)]_____ ___ ___ {1.6.7#stable}
|_ -| . [)] | .'| . |
|___|_ [,]_|_|_|__,| _||_|V... |_| https://sqlmap.orgUsage: python3 sqlmap [options]Options:-h, --help Show basic help message and exit-hh Show advanced help message and exit--version Show program's version number and exit-v VERBOSE Verbosity level: 0-6 (default 1)Target:At least one of these options has to be provided to define thetarget(s)-u URL, --url=URL Target URL (e.g. "http://www.site.com/vuln.php?id=1")-d DIRECT Connection string for direct database connection-l LOGFILE Parse target(s) from Burp or WebScarab proxy log file-m BULKFILE Scan multiple targets given in a textual file-r REQUESTFILE Load HTTP request from a file-g GOOGLEDORK Process Google dork results as target URLs-c CONFIGFILE Load options from a configuration INI fileRequest:These options can be used to specify how to connect to the target URL==这些选项可以指定如何连接到目标URL(即支持自定义构造数据包)==-A AGENT, --user.. HTTP User-Agent header value-H HEADER, --hea.. Extra header (e.g. "X-Forwarded-For: 127.0.0.1")--method=METHOD Force usage of given HTTP method (e.g. PUT)--data=DATA Data string to be sent through POST (e.g. "id=1")--param-del=PARA.. Character used for splitting parameter values (e.g. &)--cookie=COOKIE HTTP Cookie header value (e.g. "PHPSESSID=a8d127e..")--cookie-del=COO.. Character used for splitting cookie values (e.g. ;)--live-cookies=L.. Live cookies file used for loading up-to-date values--load-cookies=L.. File containing cookies in Netscape/wget format--drop-set-cookie Ignore Set-Cookie header from response--mobile Imitate smartphone through HTTP User-Agent header--random-agent Use randomly selected HTTP User-Agent header value--host=HOST HTTP Host header value--referer=REFERER HTTP Referer header value--headers=HEADERS Extra headers (e.g. "Accept-Language: fr\nETag: 123")--auth-type=AUTH.. HTTP authentication type (Basic, Digest, Bearer, ...)--auth-cred=AUTH.. HTTP authentication credentials (name:password)--auth-file=AUTH.. HTTP authentication PEM cert/private key file--ignore-code=IG.. Ignore (problematic) HTTP error code (e.g. 401)--ignore-proxy Ignore system default proxy settings--ignore-redirects Ignore redirection attempts--ignore-timeouts Ignore connection timeouts--proxy=PROXY Use a proxy to connect to the target URL--proxy-cred=PRO.. Proxy authentication credentials (name:password)--proxy-file=PRO.. Load proxy list from a file--proxy-freq=PRO.. Requests between change of proxy from a given list--tor Use Tor anonymity network--tor-port=TORPORT Set Tor proxy port other than default--tor-type=TORTYPE Set Tor proxy type (HTTP, SOCKS4 or SOCKS5 (default))--check-tor Check to see if Tor is used properly--delay=DELAY Delay in seconds between each HTTP request--timeout=TIMEOUT Seconds to wait before timeout connection (default 30)--retries=RETRIES Retries when the connection timeouts (default 3)--retry-on=RETRYON Retry request on regexp matching content (e.g. "drop")--randomize=RPARAM Randomly change value for given parameter(s)--safe-url=SAFEURL URL address to visit frequently during testing--safe-post=SAFE.. POST data to send to a safe URL--safe-req=SAFER.. Load safe HTTP request from a file--safe-freq=SAFE.. Regular requests between visits to a safe URL--skip-urlencode Skip URL encoding of payload data--csrf-token=CSR.. Parameter used to hold anti-CSRF token--csrf-url=CSRFURL URL address to visit for extraction of anti-CSRF token--csrf-method=CS.. HTTP method to use during anti-CSRF token page visit--csrf-retries=C.. Retries for anti-CSRF token retrieval (default 0)--force-ssl Force usage of SSL/HTTPS--chunked Use HTTP chunked transfer encoded (POST) requests--hpp Use HTTP parameter pollution method--eval=EVALCODE Evaluate provided Python code before the request (e.g."import hashlib;id2=hashlib.md5(id).hexdigest()")Optimization:These options can be used to optimize the performance of sqlmap-o Turn on all optimization switches--predict-output Predict common queries output--keep-alive Use persistent HTTP(s) connections--null-connection Retrieve page length without actual HTTP response body--threads=THREADS Max number of concurrent HTTP(s) requests (default 1)Injection:These options can be used to specify which parameters to test for,provide custom injection payloads and optional tampering scripts-p TESTPARAMETER Testable parameter(s)--skip=SKIP Skip testing for given parameter(s)--skip-static Skip testing parameters that not appear to be dynamic--param-exclude=.. Regexp to exclude parameters from testing (e.g. "ses")--param-filter=P.. Select testable parameter(s) by place (e.g. "POST")--dbms=DBMS Force back-end DBMS to provided value--dbms-cred=DBMS.. DBMS authentication credentials (user:password)--os=OS Force back-end DBMS operating system to provided value--invalid-bignum Use big numbers for invalidating values--invalid-logical Use logical operations for invalidating values--invalid-string Use random strings for invalidating values--no-cast Turn off payload casting mechanism--no-escape Turn off string escaping mechanism--prefix=PREFIX Injection payload prefix string--suffix=SUFFIX Injection payload suffix string--tamper=TAMPER Use given script(s) for tampering injection dataDetection:These options can be used to customize the detection phase--level=LEVEL Level of tests to perform (1-5, default 1)--risk=RISK Risk of tests to perform (1-3, default 1)--string=STRING String to match when query is evaluated to True--not-string=NOT.. String to match when query is evaluated to False--regexp=REGEXP Regexp to match when query is evaluated to True--code=CODE HTTP code to match when query is evaluated to True--smart Perform thorough tests only if positive heuristic(s)--text-only Compare pages based only on the textual content--titles Compare pages based only on their titlesTechniques:These options can be used to tweak testing of specific SQL injectiontechniques--technique=TECH.. SQL injection techniques to use (default "BEUSTQ")--time-sec=TIMESEC Seconds to delay the DBMS response (default 5)--union-cols=UCOLS Range of columns to test for UNION query SQL injection--union-char=UCHAR Character to use for bruteforcing number of columns--union-from=UFROM Table to use in FROM part of UNION query SQL injection--dns-domain=DNS.. Domain name used for DNS exfiltration attack--second-url=SEC.. Resulting page URL searched for second-order response--second-req=SEC.. Load second-order HTTP request from fileFingerprint:-f, --fingerprint Perform an extensive DBMS version fingerprintEnumeration:These options can be used to enumerate the back-end databasemanagement system information, structure and data contained in thetables-a, --all Retrieve everything-b, --banner Retrieve DBMS banner--current-user Retrieve DBMS current user--current-db Retrieve DBMS current database--hostname Retrieve DBMS server hostname--is-dba Detect if the DBMS current user is DBA--users Enumerate DBMS users--passwords Enumerate DBMS users password hashes--privileges Enumerate DBMS users privileges--roles Enumerate DBMS users roles--dbs Enumerate DBMS databases--tables Enumerate DBMS database tables--columns Enumerate DBMS database table columns--schema Enumerate DBMS schema--count Retrieve number of entries for table(s)--dump Dump DBMS database table entries--dump-all Dump all DBMS databases tables entries--search Search column(s), table(s) and/or database name(s)--comments Check for DBMS comments during enumeration--statements Retrieve SQL statements being run on DBMS-D DB DBMS database to enumerate-T TBL DBMS database table(s) to enumerate-C COL DBMS database table column(s) to enumerate-X EXCLUDE DBMS database identifier(s) to not enumerate-U USER DBMS user to enumerate--exclude-sysdbs Exclude DBMS system databases when enumerating tables--pivot-column=P.. Pivot column name--where=DUMPWHERE Use WHERE condition while table dumping--start=LIMITSTART First dump table entry to retrieve--stop=LIMITSTOP Last dump table entry to retrieve--first=FIRSTCHAR First query output word character to retrieve--last=LASTCHAR Last query output word character to retrieve--sql-query=SQLQ.. SQL statement to be executed--sql-shell Prompt for an interactive SQL shell--sql-file=SQLFILE Execute SQL statements from given file(s)Brute force:These options can be used to run brute force checks--common-tables Check existence of common tables--common-columns Check existence of common columns--common-files Check existence of common filesUser-defined function injection:These options can be used to create custom user-defined functions--udf-inject Inject custom user-defined functions--shared-lib=SHLIB Local path of the shared libraryFile system access:These options can be used to access the back-end database managementsystem underlying file system--file-read=FILE.. Read a file from the back-end DBMS file system--file-write=FIL.. Write a local file on the back-end DBMS file system--file-dest=FILE.. Back-end DBMS absolute filepath to write toOperating system access:These options can be used to access the back-end database managementsystem underlying operating system--os-cmd=OSCMD Execute an operating system command--os-shell Prompt for an interactive operating system shell--os-pwn Prompt for an OOB shell, Meterpreter or VNC--os-smbrelay One click prompt for an OOB shell, Meterpreter or VNC--os-bof Stored procedure buffer overflow exploitation--priv-esc Database process user privilege escalation--msf-path=MSFPATH Local path where Metasploit Framework is installed--tmp-path=TMPPATH Remote absolute path of temporary files directoryWindows registry access:These options can be used to access the back-end database managementsystem Windows registry--reg-read Read a Windows registry key value--reg-add Write a Windows registry key value data--reg-del Delete a Windows registry key value--reg-key=REGKEY Windows registry key--reg-value=REGVAL Windows registry key value--reg-data=REGDATA Windows registry key value data--reg-type=REGTYPE Windows registry key value typeGeneral:These options can be used to set some general working parameters-s SESSIONFILE Load session from a stored (.sqlite) file-t TRAFFICFILE Log all HTTP traffic into a textual file--answers=ANSWERS Set predefined answers (e.g. "quit=N,follow=N")--base64=BASE64P.. Parameter(s) containing Base64 encoded data--base64-safe Use URL and filename safe Base64 alphabet (RFC 4648)--batch Never ask for user input, use the default behavior--binary-fields=.. Result fields having binary values (e.g. "digest")--check-internet Check Internet connection before assessing the target--cleanup Clean up the DBMS from sqlmap specific UDF and tables--crawl=CRAWLDEPTH Crawl the website starting from the target URL--crawl-exclude=.. Regexp to exclude pages from crawling (e.g. "logout")--csv-del=CSVDEL Delimiting character used in CSV output (default ",")--charset=CHARSET Blind SQL injection charset (e.g. "0123456789abcdef")--dump-format=DU.. Format of dumped data (CSV (default), HTML or SQLITE)--encoding=ENCOD.. Character encoding used for data retrieval (e.g. GBK)--eta Display for each output the estimated time of arrival--flush-session Flush session files for current target--forms Parse and test forms on target URL--fresh-queries Ignore query results stored in session file--gpage=GOOGLEPAGE Use Google dork results from specified page number--har=HARFILE Log all HTTP traffic into a HAR file--hex Use hex conversion during data retrieval--output-dir=OUT.. Custom output directory path--parse-errors Parse and display DBMS error messages from responses--preprocess=PRE.. Use given script(s) for preprocessing (request)--postprocess=PO.. Use given script(s) for postprocessing (response)--repair Redump entries having unknown character marker (?)--save=SAVECONFIG Save options to a configuration INI file--scope=SCOPE Regexp for filtering targets--skip-heuristics Skip heuristic detection of vulnerabilities--skip-waf Skip heuristic detection of WAF/IPS protection--table-prefix=T.. Prefix used for temporary tables (default: "sqlmap")--test-filter=TE.. Select tests by payloads and/or titles (e.g. ROW)--test-skip=TEST.. Skip tests by payloads and/or titles (e.g. BENCHMARK)--web-root=WEBROOT Web server document root directory (e.g. "/var/www")Miscellaneous:These options do not fit into any other category-z MNEMONICS Use short mnemonics (e.g. "flu,bat,ban,tec=EU")--alert=ALERT Run host OS command(s) when SQL injection is found--beep Beep on question and/or when vulnerability is found--dependencies Check for missing (optional) sqlmap dependencies--disable-coloring Disable console output coloring--list-tampers Display list of available tamper scripts--no-logging Disable logging to a file--offline Work in offline mode (only use session data)--purge Safely remove all content from sqlmap data directory--results-file=R.. Location of CSV results file in multiple targets mode--shell Prompt for an interactive sqlmap shell--tmp-dir=TMPDIR Local directory for storing temporary files--unstable Adjust options for unstable connections--update Update sqlmap--wizard Simple wizard interface for beginner users
[01:20:03] [WARNING] your sqlmap version is outdated┌──(kali㉿kali)-[~]
上一篇:Promise介绍和详解
下一篇:TCP思维导图总结
相关内容
热门资讯
电视安卓系统哪个品牌好,哪家品...
你有没有想过,家里的电视是不是该升级换代了呢?现在市面上电视品牌琳琅满目,各种操作系统也是让人眼花缭...
安卓会员管理系统怎么用,提升服...
你有没有想过,手机里那些你爱不释手的APP,背后其实有个强大的会员管理系统在默默支持呢?没错,就是那...
安卓系统软件使用技巧,解锁软件...
你有没有发现,用安卓手机的时候,总有一些小技巧能让你玩得更溜?别小看了这些小细节,它们可是能让你的手...
安卓系统提示音替换
你知道吗?手机里那个时不时响起的提示音,有时候真的能让人心情大好,有时候又让人抓狂不已。今天,就让我...
安卓开机不了系统更新
手机突然开不了机,系统更新还卡在那里,这可真是让人头疼的问题啊!你是不是也遇到了这种情况?别急,今天...
安卓系统中微信视频,安卓系统下...
你有没有发现,现在用手机聊天,视频通话简直成了标配!尤其是咱们安卓系统的小伙伴们,微信视频功能更是用...
安卓系统是服务器,服务器端的智...
你知道吗?在科技的世界里,安卓系统可是个超级明星呢!它不仅仅是个手机操作系统,竟然还能成为服务器的得...
pc电脑安卓系统下载软件,轻松...
你有没有想过,你的PC电脑上安装了安卓系统,是不是瞬间觉得世界都大不一样了呢?没错,就是那种“一机在...
电影院购票系统安卓,便捷观影新...
你有没有想过,在繁忙的生活中,一部好电影就像是一剂强心针,能瞬间让你放松心情?而我今天要和你分享的,...
安卓系统可以写程序?
你有没有想过,安卓系统竟然也能写程序呢?没错,你没听错!这个我们日常使用的智能手机操作系统,竟然有着...
安卓系统架构书籍推荐,权威书籍...
你有没有想过,想要深入了解安卓系统架构,却不知道从何下手?别急,今天我就要给你推荐几本超级实用的书籍...
安卓系统看到的炸弹,技术解析与...
安卓系统看到的炸弹——揭秘手机中的隐形威胁在数字化时代,智能手机已经成为我们生活中不可或缺的一部分。...
鸿蒙系统有安卓文件,畅享多平台...
你知道吗?最近在科技圈里,有个大新闻可是闹得沸沸扬扬的,那就是鸿蒙系统竟然有了安卓文件!是不是觉得有...
宝马安卓车机系统切换,驾驭未来...
你有没有发现,现在的汽车越来越智能了?尤其是那些豪华品牌,比如宝马,它们的内饰里那个大屏幕,简直就像...
p30退回安卓系统
你有没有听说最近P30的用户们都在忙活一件大事?没错,就是他们的手机要退回安卓系统啦!这可不是一个简...
oppoa57安卓原生系统,原...
你有没有发现,最近OPPO A57这款手机在安卓原生系统上的表现真是让人眼前一亮呢?今天,就让我带你...
安卓系统输入法联想,安卓系统输...
你有没有发现,手机上的输入法真的是个神奇的小助手呢?尤其是安卓系统的输入法,简直就是智能生活的点睛之...
怎么进入安卓刷机系统,安卓刷机...
亲爱的手机控们,你是否曾对安卓手机的刷机系统充满好奇?想要解锁手机潜能,体验全新的系统魅力?别急,今...
安卓系统程序有病毒
你知道吗?在这个数字化时代,手机已经成了我们生活中不可或缺的好伙伴。但是,你知道吗?即使是安卓系统,...
奥迪中控安卓系统下载,畅享智能...
你有没有发现,现在汽车的中控系统越来越智能了?尤其是奥迪这种豪华品牌,他们的中控系统简直就是科技与艺...
